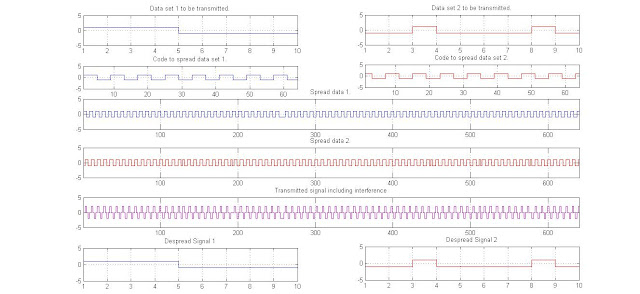
Finally, the time has come, where all our hard work spent on the project is showcased for all to see. In the form of a poster, lab book and this blog (along with a few real time practical simulations), we present our findings of how DSSS in 3G communications is possible. Our main focus with this project was the CDMA modulation technique, which is widely used in industry. Without this modulation technique it would be difficult to transmit the Data securely and efficiently.
A lot has been learnt about how Matlab can be used to simulate physical systems, which can be vital in helping with the design process and to ensure the system works before implementing it.

.jpg)